* I've lost the password to my Windows Administrator account, how do I get it back?
Question: When I set up my machine I did set a password for the Administrator account, and then I promptly forgot it, since I never use that account. Now I need it. What can I do?
Windows NT stores its user information, including crypted versions of the passwords, in a file called 'sam', usually found in \windows\system32\config. This file is a part of the registry, in a binary format previously undocumented, and not easily accessible. But thanks to a German(?) named B.D, I've now made a program that understands the registry.
This is a utility to (re)set the password of any user that has a valid (local) account on your Windows NT/2k/XP/Vista etc system.
You do not need to know the old password to set a new one.
It works offline, that is, you have to shutdown your computer and boot off a floppydisk or CD or another system.
Will detect and offer to unlock locked or disabled out user accounts!
There is also a registry editor and other registry utilities that works under linux/unix, and can be used for other things than password editing.
First download and burn the cd: Bootable CD image
This is actually a highly customized version of Linux, that's designed to do exactly what the name implies: allow you to examine and edit the password information and registry of a Windows machine.
Boot from that CD you just burned. You'll end up with something like this on your screen:
Don't let all the stark plain text worry you, the process for what we're doing is actually pretty simple.
Here's the relevant portion of that screen, enlarged:
You can see that the utility has found multiple disks and/or partitions, and is asking which one I want to work on. In my case I know that the partition listed as the larger 1 (74207MB) is my Windows drive, so I enter 2 to select it and press Enter. Next:
After selecting the disk we want to use, the utility now asks us for the location of the registry. The utility has correctly guessed the location, Windows/system32/config, so all I need to is press Enter to move on.
Next it asks more specifically what it is we want to operate on:
In this case the default answer Password reset, which indicates which portions of the system are to be worked on, is the correct one so all I need to do is press Enter.
Now it asks what we want to do:
We're here specifically to operate on passwords, so once again the default answer of 1 is correct, and I simply press Enter.
Now things get interesting.
You can see here that the utility has listed all the user accounts on my machine: Administrator, Guest, and the account I actually login with, "LeoN".
It's asking which user account to operate on, and supplied "Administrator" as the default, so once again I press Enter, and we get to the reason we're here:
Now, obviously there are several choices here. My preference is to clear the password so that no password would be required to login, and of course make sure that the account is enabled. Once done, you can then login to the account in Windows and select a new password.
Use the "Quit" options and further prompts to save data to disk, exit the utility and reboot back into Windows.
Reboot from CD, press enter (in most cases) a few times, and *poof* ... the administrator account password is reset and you have access once again.
So easy anyone could do it.
Anyone.
This is where you should be concerned.
Anyone with physical access to your machine can do what I've just described.
If you're in a position where folks with a motive or other random strangers can access your machine, you may want to rethink your physical security.
If it's not physically secure, it's not secure.
The ability to walk up with a CD, and "own" the machine with a reboot and a few keystrokes hopefully makes that pretty clear.
Friday, May 15, 2009 | 0 Comments
* How Gmail's UNDO SEND works ?
Question: Google added an "undo" to their send button. How can that work? We know that once you send an email it's out of your control?
GMail's "undo send" is not really an "undo" at all. It's certainly helpful, but it's not what you might think.
The undo send feature, which you'll find in Settings -> Labs, is really more like a "delay before sending" feature. When enabled, it "holds on" to your email for 5 seconds before the email is really sent.
 5 seconds.
5 seconds.
That's all the time you have to rethink your send.
After that time has elapsed, there is no undo.
It works because GMail doesn't actually send your mail for 5 seconds. They're holding on to it before sending it, in case you want to change your mind.
This is actually very similar to a technique mentioned by Outlook users, where you can set up a rule to delay the send of a message by some amount of time. Change your mind within that time, and you can stop Outlook from sending your message.
once your email has actually been sent, there's no way to "undo" it; there's no way to get it back.
Think before you send. No matter what.

Thursday, May 14, 2009 | 0 Comments
* How to change router's password ?
Question: How does one change the router password? Where are the controls and settings for the router ?
I recently wrote about several steps you should take to secure your router. One of those steps is to change the default password.
Several people wrote in to ask how to do that, as it's not at all clear how you access your router settings at all, much less the password screen.
I'll show you, step by step, how I access the settings on my LinkSys router
.
•
Now, I have to start by saying that unless you have a LinkSys, perhaps even the exact same model, your steps may be somewhat different. You really should be checking the documentation that comes with your router to get the specifics necessary to change settings on your device.
That being said, the concepts are generally the same for most consumer routers, and hopefully this will help you interpret those instructions a little more easily.
We start with your browser.
Routers don't have applications
or settings that you'll find on your computer anywhere. They're a separate device on your network, and as such need to be accessed across the network. Most router manufacturers have made this fairly easy by including a mini web-server inside the box that you use to access the settings.
You access your router's settings by entering its IP address in the address bar of your browser:
192.168.1.1 is a pretty common IP address for routers on small networks, but if that's not it, another "trick" that occasionally works is to open up a command prompt, enter "ipconfig" (followed by Enter), and look for a "default gateway":
Ethernet adapter Local Area Connection 2:
Connection-specific DNS Suffix . :
IP Address. . . . . . . . . . . . : 192.168.1.5
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.1.1
In most cases, that's the IP address of your router.
Once you've entered your router's IP address into your browser's address bar and pressed "Enter", you should get an authorization request:
LinkSys router requesting authorization
Most all manufacturers have default settings for this. For example, if you have a LinkSys, the default is to leave the User name blank, and enter "admin" as the password. It's this very default setting that we're going to change, because as you can see - everyone knows it.
Once you enter the correct user name and password, press OK and you should land on your routers "home page" for configuration.
Wednesday, May 13, 2009 | 0 Comments
* Is it safe to use hibernate all the time ?
Question: I have XP on my laptop. Hibernate is enabled with option enabled to Hibernate when I close lid. Is there any downside to using this routinely to power down or should I Shut Down or Restart periodically?
The theory behind hibernate is actually wonderfully simple. To oversimplify, (of course), when you hibernate the machine writes a complete image of its system RAM to the hard disk and turns itself completely off. There are two advantages to this:
*
It's off. It's using no power.
*
Turning it back on is faster than a full reboot.
That last point is the big appeal. It's accomplished because (once again, oversimplifying) the computer simply reloads the RAM image, and resumes from where you left off.
It actually is close to being that simple, and in theory it should always just work.
However, theory and practice don't always coincide.
There are actually several flies in the hibernate ointment. While it's definitely been getting better over time, you can still have problems.
The ability to hibernate, and standby for that matter, relies in part on support from the computer's BIOS. The problem is that some BIOS's aren't quite up to snuff when it comes to hibernate. This is, fortunately, one of the areas of greatest improvement in recent years, and is typically an issue only in older machines. Even then, it's not uncommon that a BIOS update can resolve many of the issues.
More common are issues with drivers for the various hardware that might be attached to your computer.
**************
Let's take a common sticking point: wireless networking
Just before you hibernate you'll likely have a working wireless connection
. That connection is, of course, terminated when your machine goes into hibernation.
When you wake up or resume from hibernate that wireless connection needs to be restored from being completely powered off to whatever state it was in before hibernation. Normally, when the device is powered in it can assume that it's in a boot situation and can simply start from scratch. Unfortunately, resuming from a hibernate isn't "from scratch". The wireless connection must, if at all possible, act as if nothing happened. In addition, your computer might wake up from hibernate in a completely different location - in which case the wireless driver needs to act as if, well, something happened; something that's not quite a reboot, but certainly ... something.
It gets complicated.
And, in fact, almost every driver for every device connected to your computer somehow needs to deal with all this in ways that are specific to each device. Some, like perhaps a monitor or screen, need very little thought. Others, like network connections that need to act like nothing happened, except that the world they're connected to could be completely different, take a little, or a lot more work.
Which means that every driver is a potential point of failure for a clean resume from hibernation.
This, too, has been getting better over time, but we're certainly not living in a perfect world.
So the first answer to your question is simply this: there's nothing wrong with always using hibernation as much as you like, unless you find that it doesn't work, or that problems result. If it works, it's nifty and faster and as you said, more convenient than opening up all those applications each time you turn on the machine.
The second answer really boils down to how long you can leave Windows running continuously without a problem. Once again in theory, forever. And once again in practice: not so much. This is particularly due to applications that don't release resources the way they should - occasionally even applications that are part of Windows itself - you simply need to reboot to clean things out. How often depends on many, many things including the hardware and software installed and how you use the machine. As one data point, I'll typically leave my relatively active desktop computer running for weeks at a time.
Usually until a Windows Update comes along that requires a reboot and resolves the question for me.
If that update-related reboot doesn't come along you may find that, once in a while, you'll want to reboot .. just because.
Wednesday, May 13, 2009 | 0 Comments
* Send a file to your favorite folder
when you a select a file in Microsoft windows OS , you can see the option "send to" in right click popup menu. In that popup menu defaulty you have following option
- compressed (zipped ) folder
- Desktop ( create shortcut )
- Mail Recipient
- My Documents
- DVD/CD-RW drive (F:)
we can remove unwanted options from that menu, and we can also add our favorite folders to that menu.
select your favourite folder
create shortcut using , ctrl + shift + drag.

move that short cut to C:\Documents and Settings\Your account name\SendTo
By default SendTo is hidden file, you have to enable "show hidden files" in folder options( windows explorer -> tools -> folder options or control panel -> folder options )
Rename that file to your favorite name.

now send file to your favourite folder easily.

Sunday, May 10, 2009 | 0 Comments
* what is MSO Cache ??
Question: I have a hidden file called MSO Cache on my E drive. Windows XP is installed on the C drive. Msocache is about 200 megabytes but it looks kind of important. I'm sure I didn't make it nor anybody else. Is it a system file or spyware? What does it do and can I delete it safely?
Msocache is another of those "magical" directories (not a file) that somehow just appears one day. Since we're not looking for this kind of thing constantly it's easy to miss exactly when it showed up.
Yep. Microsoft Office is trying to be helpful.
First, Microsoft does have a Knowledgebase article on this, though the title's not particularly helpful: Local Install Source (Msocache).
The bottom line is that it's simple a local copy of Microsoft Office's installation source. Put another way, it's a copy of portions of the Microsoft Office installation CD. Why? so that you don't have to insert the CD when you add a feature, perform a repair operation, or install service packs and patches.
Msocache is created, quoting the KB article:
...if the following conditions are true:
One of the available hard drives
has more than 1.5 gigabytes (GB) of free disk space available.
The hard disk with sufficient space is not a removable drive or a network drive.
Personally that seems kind of arbitrary, but there ya go.
You can delete the folder, but, that same Knowledgebase article goes on to say, "Never delete the MSOCACHE folder by using Microsoft Windows
Explorer." Why, I do not know. They suggest using the Windows Disk Cleanup Wizard.
Sunday, May 10, 2009 | 0 Comments
* Restore Missing folders in Group Policy editor in windows
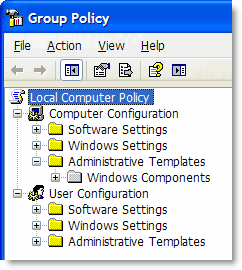
When you open the Group Policy Editor in Windows XP Professional, some of the categories under Administrative Templates may be missing. For example when you expand Administrative Templates, the System category may be missing. This article provides information on how to restore the missing folders to the Group Policy Editor.
Add the Missing ADM File
Method 1
1. Open the Group Policy Editor (gpedit.msc)
2. Expand Computer Configuration
3. Right-click Administrative Templates, and click Add/Remove Templates…
4. Click Add…
5. Select the file system.adm and click Open
6. Click Close.
Method 2
Using Windows Explorer, copy the file system.adm from the C:\Windows\INF folder to C:\Windows\system32\GroupPolicy folder. In a standard Windows XP installation, the target folder has the following ADM files by default:
conf.adm
inetres.adm
wmplayer.adm
wuau.adm
system.adm
Copying the missing file from the ADM folder should restore the missing folder in the Group Policy Editor. If that does not work, make sure that filtering is turned off.
Turn Off Filtering
1. Expand Computer Configuration, and select Administrative Templates
2. From the View menu, click Filtering…
3. Uncheck the following checkboxes:
Filter by Requirements information
Only show configured Policy settings
4. Click OK.
Saturday, May 09, 2009 | 0 Comments
* Network Simulator - NS2 installation
Ns is a discrete event simulator targeted at networking research. Ns provides substantial support for simulation of TCP, routing, and multicast protocols over wired and wireless (local and satellite) networks.
download latest NS2 installation files at this link
http://sourceforge.net/project/showfiles.php?group_id=149743&package_id=169689&release_id=588643
NS2 INSTALLATION:
$su
password:
$ cd /opt
$ tar -xvf ns-allinone-2.33.tar.
$ cd ns-allinone-2.33
$ ./install
after 15 min installatin wil complts
by
giving this suggestions
Ns-allinone package has been installed successfully.
Here are the installation places:
tcl8.4.18:
/opt/ns-allinone-2.33/{bin,include,lib}
tk8.4.18:
/opt/ns-allinone-2.33/{bin,include,lib}
otcl:
/opt/ns-allinone-2.33/otcl-1.13
tclcl:
/opt/ns-allinone-2.33/tclcl-1.19
ns:
/opt/ns-allinone-2.33/ns-2.33/ns
nam: /opt/ns-allinone-2.33/nam-1.13/nam
xgraph: /opt/ns-allinone-2.33/xgraph-12.1
gt-itm: /opt/ns-allinone-2.33/itm, edriver, sgb2alt, sgb2ns, sgb2comns, sgb2hierns
----------------------------------------------------------------------------------
Please put /opt/ns-allinone-2.33/bin:/opt/ns-allinone-2.33/tcl8.4.18/unix:/opt/ns-
allinone-2.33/tk8.4.18/unix
into your PATH environment; so that you'll be able to run itm/tclsh/wish/xgraph.
IMPORTANT NOTICES:
(1) You MUST put /opt/ns-allinone-2.33/otcl-1.13, /opt/ns-allinone-2.33/lib,
into your LD_LIBRARY_PATH environment variable.
If it complains about X libraries, add path to your X libraries
into LD_LIBRARY_PATH.
If you are using csh, you can set it like:
setenv LD_LIBRARY_PATH
If you are using sh, you can set it like:
export LD_LIBRARY_PATH=
(2) You MUST put /opt/ns-allinone-2.33/tcl8.4.18/library into yourTCL_LIBRARY environmental
variable. Otherwise ns/nam will complain during startup.
After these steps, you can now run the ns validation suite with
cd ns-2.33; ./validate
For trouble shooting, please first read ns problems page
http://www.isi.edu/nsnam/ns/ns-problems.html. Also search the ns mailing list archive
for related posts.
But don't mind dat message open u r bash
do
password:
OTCL_LIB=/opt/ns-allinone-2.33/otcl-1.13
NS2_LIB=/opt/ns-allinone-2.33/lib
X11_LIB=/usr/X11R6/lib
USR_LOCAL_LIB=/usr/local/lib
export LD_LIBRARY_PATH=$LD_LIBRARY_PATH:$OTCL_LIB:$NS2_LIB:$X11_LIB:
$USR_LOCAL_LIB
# TCL_LIBRARY
TCL_LIB=/opt/ns-allinone-2.33/tcl8.4.18/library
USR_LIB=/usr/lib
export TCL_LIBRARY=$TCL_LIB:$USR_LIB
# PATH
XGRAPH=/opt/ns-allinone-2.33/bin:/opt/ns-allinone-2.33/tcl8.4.18/unix:/opt/ns-
allinone-2.33/tk8.4.18/unix
NS=/opt/ns-allinone-2.33/ns-2.33/
NAM=/opt/ns-allinone-2.33/nam-1.13/
PATH=$PATH:$XGRAPH:$NS:$NAM
final step:
#./validate
if u have taken any other folder as extraction path will be changed.
Saturday, May 09, 2009 | 0 Comments
* Using wine to run windows application on openSUSE 11.0

Do you know how to run a windows application on Linux? Wine is one of many emulator programs. It was operating in different Linux distribution and can simulate most of the windows application. Either office or some sharing software which can be simulated via wine on Linux platform. You can follow the steps below to install and run it, if you want to try it now.
Installation
# zypper install wine
Now, you need to run this command to configure your wine environment
# winecfg
If you want to use wine by gui, please install wine-doors
# zypper install wine-doors
You can see the following wine-doors gui after installation.
Wine Doors will appear Initial Setup window when you run it.
Congratulations! now you can start to use wine.
Below is my example of the implementation of a windows program.
# wine everest.exe
Saturday, May 09, 2009 | 0 Comments
* Converting your filesystem from ext3 to ext4

ext4 filesystem supports large volumes of files, backward compatibility with ext2 and ext3, persistent pre-allocation of on-disk space for a file, delayed allocation, journal checksumming, online defragmentation and many more such things. If that isn't enough for you, Jaunty Jackalope has been a very fast, powerful and beautiful distro version of Ubuntu that everyone is appreciating.
1. boot the computer from the Ubuntu 9.04 Desktop CD
2. Once you are booted into the live environment, run the following command replacing /dev/DEV with the drive partition that you want to upgrade.
tune2fs -O extents,uninit_bg,dir_index /dev/DEV
[NOTE : the -O is the capital letter O, not zero]
3. You then need to run fsck to fix up some on-disk structures that tune2fs has modified.
e2fsck -fD /dev/DEV
4. Next, mount the drive
mount -t ext4 /dev/DEV /mnt
5. Edit fstab and change ext3 to ext4 on the drive you upgraded
UUID=xxxx / ext4 relatime,errors=remount-ro 0 1
6. Finally, you need to run grub-install on your new partition. The version of grub that shipped with Ubuntu 8.10 cannot boot from ext4 partitions so if you skip this step, your computer won't boot.
grub-install /dev/DEV –root-directory=/mnt –recheck
7. Now reboot the computer and enjoy your new ext4 filesystem
Saturday, May 09, 2009 | 0 Comments
* How to mount ISO image in linux ??

Due to the current design of hard disk capacity growing in volume, at every turn on more than 500GB, there are more and more people do not like the comparison to burn out some of the information, whether or important documents had been stored some of the ISO file Of course, many of the windows users always use alcohol by one set of software simulation to mount ISO image, but how to mount ISO image in Linux? Actually, there is a simple way to mount ISO image via command line in Linux system, you just need type a few under commands to mount it that will be more convenient than windows, if you want to mount ISO image for access information in your Linux machine, whether openSUSE or Ubuntu, you can enter the following command to do it now.
# cd /mnt
# mkdir cdrom
# mount /root/Desktop/gos-3.0-gadgets-20080924.iso /mnt/cdrom -o loop
Saturday, May 09, 2009 | 0 Comments
* Changin MAC address of PC
LINUX:
1) Bring down the interface: "ifconfig eth0 down"
2) Enter new MAC address: "ifconfig eth0 hw ether 00:00:00:AA:AA:AA"
3) Bring up the interface: "ifconfig eth0 up"
MAC OS X:
sudo ifconfig en0 lladdr 00:00:00:00:00:01
BSD
1) Bring down the interface: "ifconfig xl0 down"
2) Enter new MAC address: "ifconfig xl0 link 00:00:00:AA:AA:AA"
3) Bring up the interface: "ifconfig xl0 up"
Windows 2000/XP
Method 1:
This is depending on the type of Network Interface Card (NIC) you have. If you have a card that doesn't support Clone MAC address, then you have to go to second method.
a) Go to Start->Settings->Control Panel and double click on Network and Dial-up Connections.
b) Right click on the NIC you want to change the MAC address and click on properties.
c) Under "General" tab, click on the "Configure" button
d) Click on "Advanced" tab
e) Under "Property section", you should see an item called "Network Address" or "Locally Administered Address", click on it.
f) On the right side, under "Value", type in the New MAC address you want to assign to your NIC. Usually this value is entered without the "-" between the MAC address numbers.
g) Goto command prompt and type in "ipconfig /all" or "net config rdr" to verify the changes. If the changes are not materialized, then use the second method.
h) If successful, reboot your system.
Method 2:
This should work on all Windows 2000/XP systems
a) Go to Start -> Run, type "regedt32" to start registry editor. Do not use "Regedit".
b) Go to "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\ Control\Class\{4D36E972-E325-11CE-BFC1-08002BE10318}". Double click on it to expand the tree. The subkeys are 4-digit numbers, which represent particular network adapters. You should see it starts with 0000, then 0001, 0002, 0003 and so on.
c) Find the interface you want by searching for the proper "DriverDesc" key.
d) Edit, or add, the string key "NetworkAddress" (has the data type "REG_SZ") to contain the new MAC address.
e) Disable then re-enable the network interface that you changed (or reboot the system).
Method 3:
Use the program Etherchange from http://ntsecurity.nu/toolbox/etherchange/
Windows 9x
Use the same method as Windows 2000/XP except for the registry key location is "HKEY_LOCAL_MACHINE\System\ CurrentControlSet\Services\Class\Net" and you must reboot your system.
Saturday, May 09, 2009 | 0 Comments
* Installing a software on Linux
One of the most difficult things to get used to in the Linux world is installing new software packages. In the world of Windows, every program comes with a Setup.exe program that asks you some very easy questions and takes care of the job for you. While Linux software can be almost that easy to install, you will sometimes find software that seems to fight every step of the way. I can't cover all the problems you might run into, but I'll try to give you the basics and a few pointers to help get you over the rough spots.
Software tends to come in "packages". In the Windows world a package is a Setup.exe or a program.zip file. On a Mac a package is a program.dmg or a program.sit file. In the Linux world, there are several kinds of packages, and each distribution has its own preferred package format.
Another popular package format is DEB, the Debian software package. Debian packages and the Advanced Packaging Tool (APT) were the first to introduce several advanced features that are now common, such as automatic dependency resolution and signed packages. Debian packages are used by Debian GNU/Linux (naturally), and distributions based on it, including Ubuntu, Knoppix, and Mepis. A Debian package file normally will be named something like program-version-other.deb
Tar Balls :
A tar ball is a (usually compressed) archive of files, similar to a Zip file on Windows or a Sit on the Mac. Tar balls come in files that end in .tar, .tar.gz, .tgz, or something along these lines. To unpack a tar ball, use this command.
[user]$ tar -xzvf filename.tar.gz
The parameters are x to extract files, z to filter through gzip for decompression (leave this off if the file does not have a gz extension), v for verbose mode so you can tell what's going on, f indicating there will be a filename to follow. You may want to create an alias called "untar" that feeds in these options if you have a hard time remembering command line options as I do.
This command will not install the software, it will only extract the archived files. It is your job then to find the README file or INSTALL file and read its instructions for installation. If the archive contains binaries there will usually be a setup script (often called install.sh) that you must execute as "SUPER USER"( using su command )
Debian, Ubuntu: APT
There is a broad array of tools for working with DEB packages, but the one you will commonly use is apt-get, arguably the easiest of Linux package management tools. apt-get is so easy because it not only keeps track of what packages are installed, but also what other packages are available. It will even download them from the Internet for you (if properly configured).
[root]# apt-get install packagename
To remove software is just as easy.
[root]# apt-get remove packagename
Although the repositories that contain installable packages might live on the Internet or on a disc somewhere, APT keeps a local database on your hard drive with a list of all available packages and where to find them. This database needs to be explicitly updated. To update the APT database:
[root]# apt-get update
A common idiom is to update your package database, and then upgrade all the packages that have patches or security updates to install. The following command will do this all at once.
[root]# apt-get update; apt-get upgrade
For a more indepth apt-get tutorial and other resources, see Managing Software with APT and dpkg.
Fedora, Red Hat: yum
yum does for RPM packages roughly what apt-get does for Debian packages. Like apt-get, yum can download and install packages from a configured repository.
[root]# yum install packagename
To remove software is just as easy.
[root]# yum remove packagename
yum does not keep a local copy of your package database by default, so normally there is no need to update it. To install all available security patches and bug fixes, use this command:
[root]# yum update
You can also explicitly update a single package with:
[root]# yum update packagename
For a more indepth yum tutorial and other resources, see Managing Software with yum and rpm.
Mandriva: urpm
Mandriva Linux (formerly Mandrake and Connectiva) has a toolset similar to APT called urpmi. To install software:
[root]# urpmi packagename
To remove software:
[root]# urpme packagename
To update the local package database:
[root]# urpmi.update -a
To install security updates and bug fixes:
[root]# urpmi --auto-select
SUSE : Yast
SUSE uses RPM as its native package format, but has its own high level tool to manage system software installation.
SUSE Linux uses a tool called yast (which allegedly is an acronym for Yet Another Setup Tool) to perform all kinds of system administration tasks, including installing software.
# yast -i gimp
# zypper in gimp
Saturday, May 09, 2009 | 0 Comments
* Task Manager disabled !
Question: My task manager has a "task manager has been disabled by the administrator" message. How did this happen and how can I correct this?
The situation's pretty simple. If you right click on the clock in the Windows taskbar, the Task Manager item is grayed out:
Or, if you try to run taskmgr.exe manually, you get this message:
So, how did this happen?
As we'll see in a moment, there are settings you can access as an administrator that would allow you to disable and enable Task Manager in this way.
You didn't do that, you say?
Then a virus probably did.
Disabling Task Manager is one way viruses try to make it harder for you to deal with their infections. Before proceeding any further, you should run a complete up to date anti-virus scan of your machine. It's possible, perhaps even likely, that you've been infected.
Once you come back virus-free, you can proceed with the fix.
•
If you have Windows XP Pro, there's a nifty user interface to directly edit the setting you want to repair. Click Start, then click Run and type in gpedit.msc:
And press OK. This runs the Group Policy Editor.
Once in the Group Policy Editor, expand in turn:
User Configuration | Administrative Templates | System | Ctrl+Alt+Del Options
You should see something much like this:
Group Policy Editor, Ctrl+Alt+Del Options
Double click on Remove Task Manager to change its setting:
It should be enough to click on Not Configured and then OK and Task Manager is available once again.
•
If you don't have Windows XP Pro, then you'll need to edit the registry manually.
Click Start, then click Run, type in regedit, and click on OK.
Expand these registry keys in turn:
HKEY_CURRENT_USER | Software | Microsoft | Windows | CurrentVersion | Policies | System
You should see something similar to this:
Right Click on the DisableTaskMgr item:
Click on Delete, confirm that you want to delete, and Task Manager should be available once again.
another method:
Click Start, Run and type this command exactly as given below: (better - Copy and paste)
REG add HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System /v DisableTaskMgr /t REG_DWORD /d 0 /f
Saturday, May 09, 2009 | 0 Comments
* Installing Firefox in Linux

This procedure is Installing firefox in Linux which is not directly connected to internet.
download latest firefox from any one of the below sites, latest release will be added in these links by mozilla corporation.
latest releases : FTP ftp://ftp.mozilla.org/pub/firefox/releases/
HTTP http://www.mozilla.com/en-US/firefox/personal.html
open a terminal/konsole and type:
CODE
$ su
<>
# mv firefox* /usr/local/bin/
# cd /usr/local/bin/
# tar -jxvf firefox*
- Log out root with the keys: Ctrl+D
- Type "kmenuedit" and you'll get a GUI where you can add an entry in --> Internet --> Web Browsers.
( NOTE: kmenuedit is for KDE based distros . . for distros that use the Gnome desktop use either "alacarte" or the "gnome-menu-editor" )
- Make a new menu entry, call it Firefox and fill in as command: /usr/local/bin/firefox/firefox
- Save
- Close kmenuedit
- Close the terminal
- And have a look in your "menu" it should be there !
( you can drag a shortcut from the menu on your desktop or "taskbar" )
if your system directly connected to internet, then you can install very easily using YAST
Friday, May 08, 2009 | 0 Comments
* Animated Penguin GRUB splash Screen

In a openSUSE linux system we can edit OS selection Screen with animated penguins.
Animated Penguin GRUB splash Screen
Procedure
- Create a temporary new directory in your home folder. (You can create it anywhere, but for simplicity, I will say the path as the home folder and the directory name as new).
- Now copy the file message from the /boot folder in this directory using the command, ‘cp /boot/message new’.
- Now change into the new directory, ‘cd new’.
- Extract the files from the archieve message using the command, ‘cpio -i < message’.
- Now minimize the terminal and open the directory new that you created. Edit the file ‘gfxboot.cfg’ using your favorite text editor.
- The file will contain a line ‘penguin=-1′ (for openSUSE 10.2) or ‘penguin=0′ (for openSUSE 10.3). Change it to ‘penguin=100′. Save the file.
- This number, 100, 0 or -1 is the probability of the penguin screen being shown. -1 is random. 0 means that penguin will never be shown and 100 means that it will be shown all the time you boot your computer.
- Coming back to the poceedings, delete the message file in the directory new by typing ‘rm message’ in the terminal.
- Now enter command ‘ls . | cpio -o > message’ to recompress the archieve.
- Now the last step, enter the command ’sudo cp message /boot’, enter your root password if required and you are done. Next time you boot up, you will be greeted by the penguins depending on the probability set by you.
- And you are done. Enjoy.
you tube link : http://www.youtube.com/watch?v=4HDyZXFakEI
Friday, May 08, 2009 | 0 Comments

